Enterprise products, solutions & services
Security is a matter of great concern for humanity. This includes personal security, which enables us to live and work in peace, and data security, which ensures the smooth running of the digital economy. However, the persistent emergence of ransomware incidents poses a threat to the development of all industries.
According to third-party statistics, up to 35.83 million ransomware attacks occurred on the global network in 2022, marking an increase of more than 13 million compared with 2021. This included many vicious large-scale ransomware incidents. It is clear that ransomware protection is needed to maintain the long-term stable development of all industries.
First, what is ransomware? Ransomware is a special type of malware. Unlike other viruses, ransomware encrypts data, and holds victims to ransom with targeted and organized network threat attacks.
The ransomware attack process consists of the following phases.
1. Detection (detection phase)
In this phase, the attacker probes the target hosts on the Internet. For example, the attacker performs proactive vulnerability scanning to find out existing unfixed vulnerabilities that can be exploited by ransomware on the hosts. Once a vulnerability is detected, the attack starts.
2. Attack implantation (spread phase)
In this phase, attackers may send virus-infected emails or phishing websites to the target's mailbox, or implant ransomware into the target's production host or storage system by exploiting detected vulnerabilities.
3. Activation (lateral movement and encryption phase)
(1) After the ransomware is successfully implanted, it starts running, obtains the key for encrypting files from the ransomware key server of the attacker, detects the network of the attack target and implements lateral movement, and spreads the ransomware to as many hosts as possible. Some ransomware with the double extortion model also uploads key data of the attack target to the attacker's server. In this phase, the ransomware is imperceptible since impact on the services of the attack target is insignificant.
(2) After obtaining and spreading the encryption key, the ransomware performs large-scale encryption operations on files (including local files and files in mounted network storage) that can be accessed by the host. Some advanced ransomware can also detect backup data in the storage system and proactively delete the backup data to prevent the attack target from recovering.
After the process is completed, the attack target will be prompted to pay ransom.
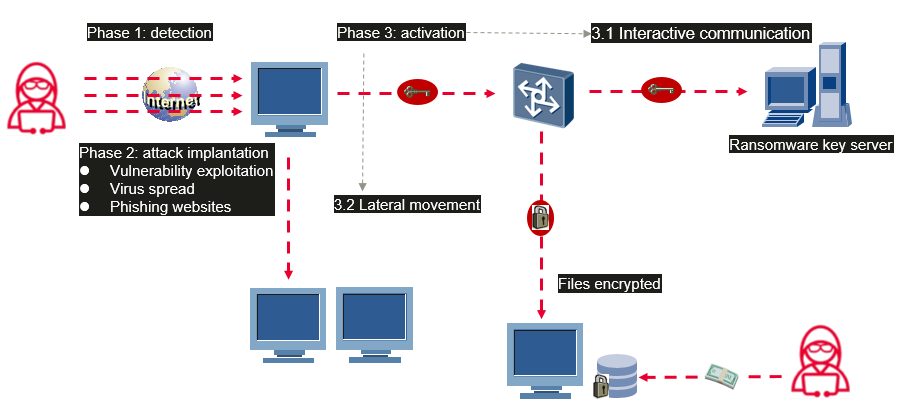
Traditional network security solutions mostly kick in only in the detection and attack implantation phase. However, with the development of remote office, mobile terminal access, supply chain ecosystem interconnection, and service cloudification, enterprise boundaries have become increasingly blurred. This means IT architecture no longer has a single and easy-to-identify boundary. As a result, border-based network security and data security face increasing challenges in policy formulation because lateral movement will become invincible once network threats such as ransomware break through a boundary. To defend against ransomware attacks, on the one hand, the protection capability on the network side needs to be improved to reduce the possibility of being broken through. On the other hand, the resilience capability of data security needs to be prompted. When the network side fails to defend against ransomware attacks, the following requirements should be met.
(1) Effective prevention of data from being encrypted
(2) Timely warning of ransomware attacks
(3) Fast service system restoration, including a complete and clean data copy after the data is encrypted
As a data carrier, storage is the last line of defense for data security. Huawei OceanStor Pacific Scale-Out Storage adopts data encryption, data tampering prevention, and detection and analysis capabilities to defend against ransomware attacks. In addition, Huawei introduces the Air Gap secure isolation zone to defend against ransomware attacks on the storage side, making them preventable, perceptible, and recoverable and greatly improving data resilience.
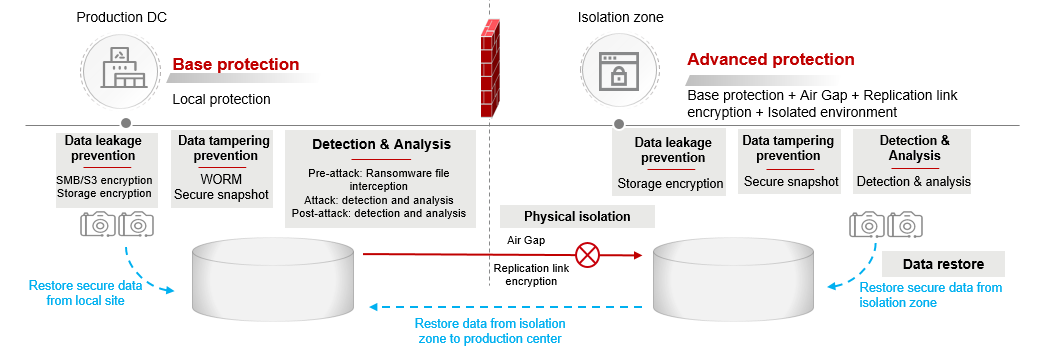
Now, let's look at some key technologies involved in Huawei OceanStor Pacific Scale-Out Storage Ransomware Protection Solution.
Encryption is a typical method to prevent sensitive information leakage in the event of raw data theft. The sensitive information cannot be leaked due to the uncrackable of encryption even if hackers obtain the data. Data encryption of OceanStor Pacific is classified into storage encryption and transmission encryption. Storage encryption prevents physical attacks (such as storage theft and hard disk theft), and transmission encryption effectively prevents data interception, theft, leakage, and tampering during transmission.
Data tampering prevention plays an important role in the OceanStor Pacific Storage Ransomware Protection Solution. In addition to preventing tampering in scenarios where unstructured data is written once and read many times, anti-tamper can also be implemented at the snapshot level in scenarios of write modification.
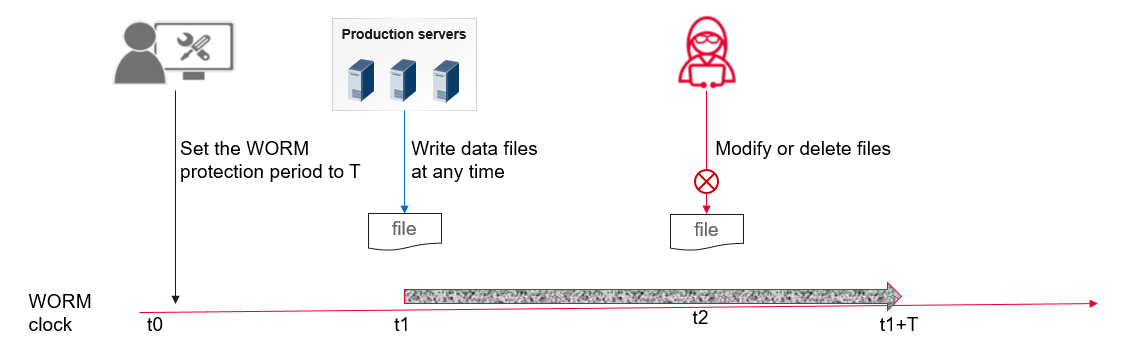
Unstructured data WORM (Write Once Read Many) means that data can be written only once and read multiple times. Users can set a protection period for files. During the protection period, files can be read only but cannot be modified or deleted. After the protection period expires, files can be deleted.
Data in both secure snapshots and common snapshots is read-only. The secure snapshot has a protection period once it is completed, distinguishing it from the common snapshot. During the protection period, even administrators do not have the permission to delete the snapshots. After the secure snapshot expires, it can be manually or automatically deleted.
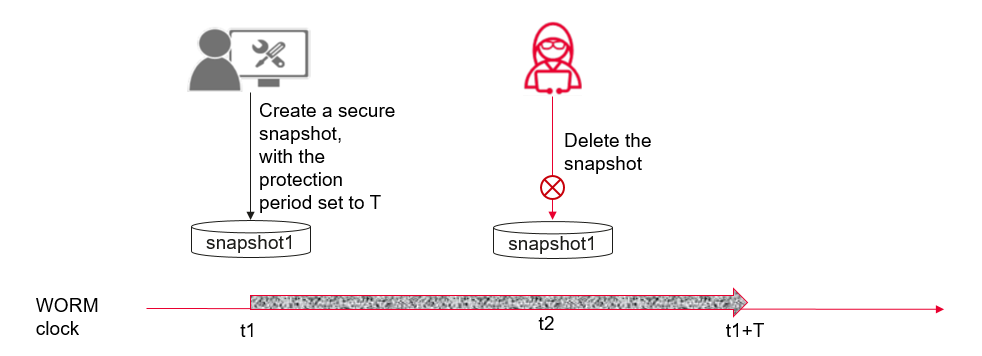
WORM clocks are adopted in both unstructured data WORM and secure snapshots. The WORM clock of the cluster can be set only once, and features the following sets. When the WORM clock is later than the system clock, the WORM clock is corrected to the system clock. However, when the WORM clock is earlier than the system clock, the maximal increasing value of WORM time per hour allowed is no more than 138 seconds. This prevents attackers from modifying the WORM clock or system clock to bypass unstructured data WORM and secure snapshot protection.
OceanStor Pacific supports write once read many (WORM) to protect unstructured data from tampering or deletion. If certain data needs to be modified in some scenarios, however, secure snapshots are needed to protect data copies, as data in WORM filesystem cannot be changed once written. In the face of ransomware attacks, it is vital for organizations to be alarmed that data is encrypted by the ransomware in a timely manner and to ensure that a secure copy of data is available for recovery. Effective detection and analysis of protected data can reduce the possibility of data encryption by ransomware and improve the success rate of data recovery.
The ransomware detection and analysis solution - running on the combination of OceanStor Pacific and OceanCyber - implements three-layer protection and detection against ransomware attacks:
√ Pre-attack (ransomware proliferation phase): Blocks the writing of files that have known ransomware extensions.
√ During attack (ransomware horizontal spread and encryption phase): Monitors the writing of known types of ransomware encrypted files, identifies malicious I/O behaviors, and uses machine learning models to determine the threat.
√ Post-attack (ransomware extortion completed): Extracts the snapshot change features of the filesystem, identifies the system from the perspective of content, and uses the machine learning model to analyze whether the filesystem is infected.
FileBlocking is a function of OceanStor Pacific used to prevent attacks and intercept files from known-ransomware sources that are capable of encryption.
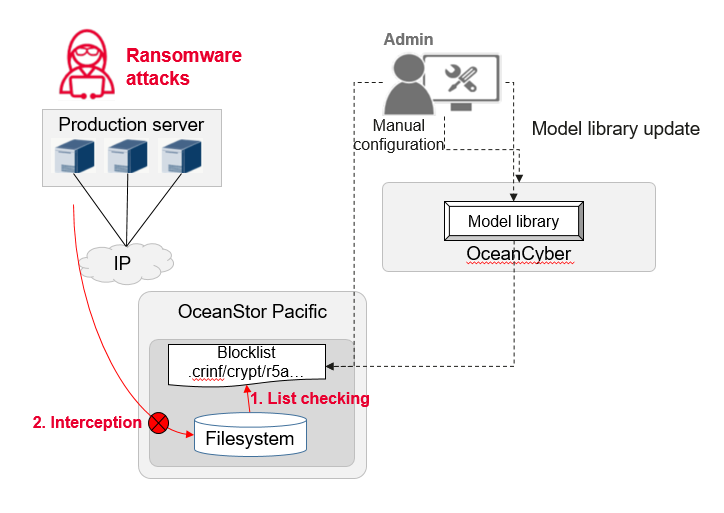
√ A blocklist is introduced in the access protocol configuration of OceanStor Pacific. It can intercept files with specific extensions, preventing these files from being written to the storage system.
√ OceanCyber is preconfigured with common detection models that contain known ransomware file extensions. These extensions can be updated by importing detection models and adding file extension filtering rules.
Ransomware attack vectors have common characteristics, such as high random read operations and forced encryption, writing, and deletion. They serve as the theoretical basis to detect abnormal I/O behavior. A typical ransomware attack vector comprises the following actions:
√ Reads the file, which is necessary to encrypt data;
√ Writes a new or rewritten file with similar read/write bytes;
√ Destroys the original information and deletes/rewrites the original file;
√ Writes shortly after or even concurrently with reads;
√ Wants to read, write and delete in a short time.
Targeted at these common features of ransomware attacks, OceanStor Pacific and OceanCyber build indicators to reflect abnormal reading and writing and encrypted file damage. By using an orderly combination of quick abnormal behavior screening and in-depth file damage detection, this solution realizes accurate detection of ransomware in storage, and solves ransomware detection problems including high confidence, wide coverage, strong timeliness, low resource overhead, and anti-extreme attack in existing storage systems.
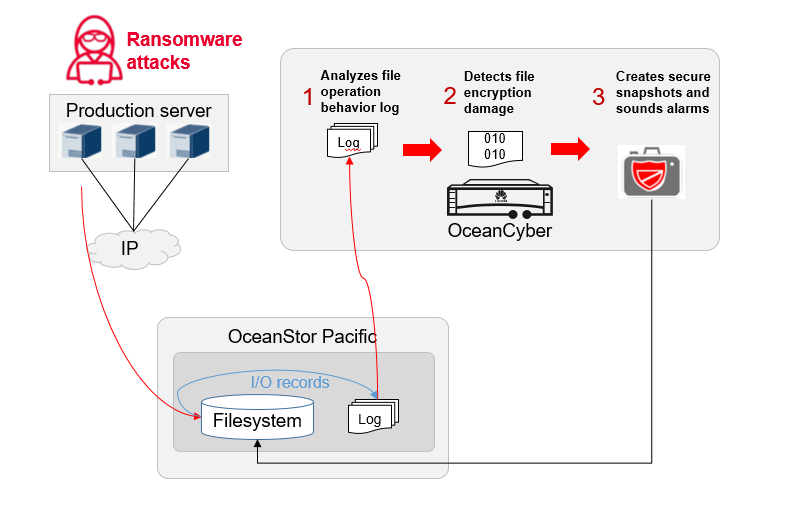
√ Quick screening of abnormal I/O behaviors
The solution analyses and identifies suspicious I/O behavior in storage systems based on common characteristics, before performing in-depth file damage detection on the related files.
√ In-depth detection of file damage
Damaged files are identified based on basic content features. For files with unidentified basic features, machine learning algorithms are run on file content to detect file damage.
√ Secure snapshots and alarms
Secure snapshots are created for the file system where damaged files are located and alarms are sounded to enable timely intervention, preventing ransomware from spreading further and reducing losses.
It is vital to secure a clean copy of data available for recovery in the event of a cyber threat. The periodic copy ransomware detection function of OceanStor Pacific and OceanCyber can be configured (daily or even hourly) to detect namespace snapshots and identify whether namespace data is infected. If the data in a snapshot is resilient, the snapshot will be set as a secure snapshot, providing a clean and reliable recovery data source that will not be deleted by ransomware.
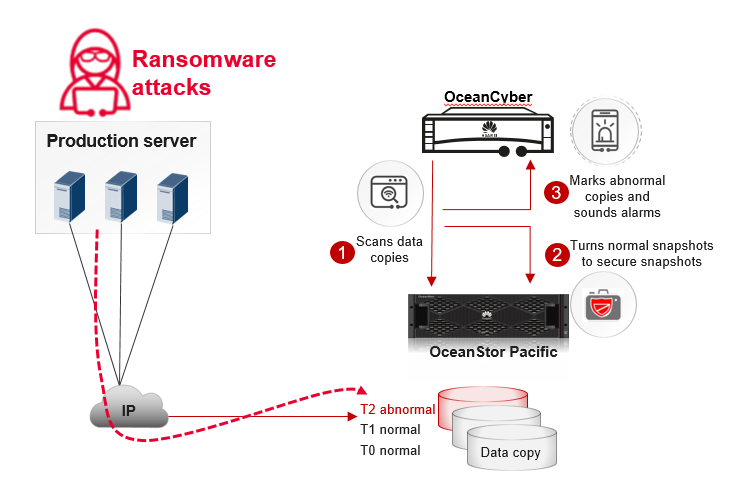
Snapshot ransomware detection includes:
√ Known ransomware feature detection in a single snapshot
There are two common behaviors of ransomware: adding a suffix to the file extension of the encrypted file and leaving a ransomware file (blackmail). For known ransomware, the suffix and blackmail characteristics can be used to find traces of ransomware infections.
√ ML-based detection of pre- and post-snapshot data change behaviors
First, based on the metadata features of snapshots, several basic change features are quickly extracted to form a baseline model. The model is used to determine whether the change of each snapshot is suspicious, and if so, the solution will extract the full change features of the snapshot and use the machine learning model for detection.
Through data encryption, anti-tampering, detection and analysis, and Air Gap (to be introduced), Huawei OceanStor Pacific builds a data protection layer that is typically not included in conventional defenses, enabling organizations and enterprises to say "no" to ransomware. As a Chinese saying goes, "while the priest climbs a post, the devil climbs ten." Since ransomware is constantly evolving, it is necessary to stay one step ahead of ever-evolving cyber threats, and Huawei OceanStor Pacific will continue to optimize solutions to protect customers' core data.
Nowadays, the vitality of data is shining in all walks of life. Data productivity has become an indispensable accelerator of world development. Huawei will continue developing innovative technologies, such as data encryption, real-time ransomware detection, and secure snapshots, to build protective walls for enterprise data across any industry.
Disclaimer: The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy, position, products, and technologies of Huawei Technologies Co., Ltd. If you need to learn more about the products and technologies of Huawei Technologies Co., Ltd., please visit our website at e.huawei.com or contact us.