This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies. Read our privacy policy>
![]()
This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies. Read our privacy policy>
![]()
Enterprise products, solutions & services
2020 changed the landscape of enterprise infrastructure, with the COVID-19 pandemic forcing workforces, customers, and business processes to adapt to a new operating model, one where remote access, untrusted networks, and data security were more complex than ever before.
The role of digital identities is absolutely pervasive and underpins many of the aspects of enterprise digital transformation. In IDC's 2019 Chief Information Officer (CIO) survey, 83% of CIOs said digital trust would be a top priority over the next five years. In addition, 64% of CIOs in Europe indicated that they have already begun implementing a trust platform.
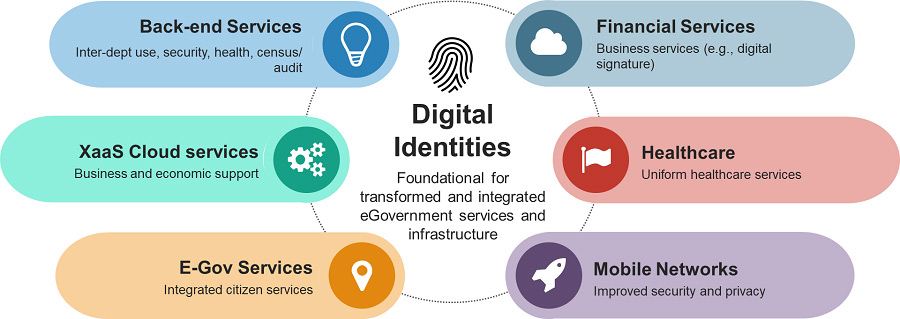
Most of the Gulf Cooperation Council (GCC) countries and their neighbors have active digital identity projects within the public sector, which lay the foundation for End to End (E2E) digital identity platforms. Advanced projects like the Emirates Identity Authority (EIDA) and UAE PASS initiatives in the United Arab Emirates — with the latter serving as the national digital identity and digital signature solution for the country — along with the National Profile project in Saudi Arabia, are the starting point for identity- and citizen-centric government digital transformation. Similar initiatives developed elsewhere in the world — including global initiatives such as the World Bank's Identification for Development (ID4D) project and Qatar's Tasmu Smart program — have highlighted multiple technology research areas, many of which use digital identities as a fundamental part of their capabilities.
In this context, the term "digital identity" does not simply refer to a system that identifies human individuals, rather to one that identifies any kind of component, even something abstract. An identity could therefore as easily refer to a person as to their car, and the association of the two identities may simply be a logical expression of ownership. Drill deeper, and every component within the vehicle can have its own digital identity too; this is, of course, nothing more than a fundamental expression of IoT and a basis for building a digital twin. The connected car is just an example, but this is far from hypothetical: many of the hundreds of connected components in a modern vehicle already use digital identities to communicate with each other and deliver telemetry and maintenance data.
Going further still, beyond discrete physical objects, and abstract entities can be defined with digital identities as well. A programming interface that is used to integrate disparate systems, such as an e-commerce site with an inventory management system for example, is itself an identity. In that model, integrating systems becomes an exercise in identity management.
By taking an identity-centric approach to infrastructure, new capabilities can be added and extended with ease. A new relationship can be expressed in terms of the constituent identities involved and their permitted interactions with other digitally-identified entities. This facilitates secure communications and transactions, both within an enterprise environment as well as with external partners, customers, and more.
Deploying a solid identity platform is a necessity for digital transformation, and the selection of technologies and partners for digital identities is one of the most important decisions a CIO will make this decade.
Consider a simple medical use case of a doctor writing a prescription for a patient. A paper script is flawed — it can be misread or misfiled and is also subject to fraud. (Digital alternatives exist, but for this example we'll start with paper and work our way up.) Replacing this simple paper document with encrypted data — data associated with the digital identities of both doctor and patient — changes the equation.
In a blockchain context, we would refer to this as publishing the prescription as a transaction on the public ledger. There are conventional ways to achieve the same result, but blockchain is well suited to identity-centric ecosystems: it enables networks of entities to make assertions on public record, available to all members of the ecosystem, yet without revealing private data beyond its intended recipient. Healthcare and financial services are natural fits here and there are numerous blockchain projects already underway in these markets globally. But the same principles can apply in many other environments. And in these cases, a managed blockchain created with a technology partner is the preferred option.
In our example, we now have a digitally identified prescription that can't be misread, one that is permanently associated with both the doctor who issued it and the patient who received it, as well as with the pharmacist who dispensed the medication. These interactions, most notably the dispensing of the medication, are irrefutable facts defined as identity interactions.
We could just as easily map these interactions to multiple enterprise business workflows. We could do the same in human resource management and asset management. And we could also do the same for physical interactions such as inventory and warehouse management, lot provenance and integrity for logistics, and so on. Everything is an identity.
Interactions between digital identities at this scale go far beyond simple user authentication: they build the foundations for networks of trust, the management of risk, and for safeguarding privacy as well as directly enabling security policies and incident detection.
To an information security practitioner, digital identities are high-value assets, which are managed carefully. Digital personas must be protected from tampering, impersonation, and disruption, any of which could expose a business to fraud, degrade services, and collapse trust. In our medical example, it's easy to see how a fraudulent identity could be used to obtain high-risk drugs or interfere in a patient's health program.
Protection of digital identities is therefore essential, but so too is oversight and monitoring. One of the core tenets of such an identity-first approach is that all interactions between identities should be audited, a concept most frequently applied in the information security world but equally applicable to operational interactions as well.
Behavioral monitoring is the practice of analyzing the activities of identities and their interactions, to ensure that their behavior is within expected parameters. Not all misuse is black and white, nor even deliberate, and analytics helps to identify and intervene when anomalies are found. While real-time analytics are key to maintaining the standard of business outcomes, historical analysis is also highly valuable, investigating the circumstances, for example, that led to a piece of machinery failing, software crashing, or a customer abandoning a transaction.
Machine Learning (ML) is a core part of this discipline, since the exponentially growing complexity of identity interactions makes it impossible to define and classify every possible combination. In fact, it's exactly that limitation which attackers use to circumvent systems, by exploiting behavioral edge cases that system administrators have not explicitly identified. ML and Artificial Intelligence (AI) can take control back, creating systems in which "normal" behavior is learned and then constantly updated, with outliers escalated for investigation.
During adverse circumstances, or in the event of a transaction being rejected, digital identities provide an essential capability: they can be used to demonstrate that a transaction was valid, revoking access to any entity or relationship that may be compromised or acting suspiciously.
Our medical example extends even further, such as providing government health departments with data concerning prescriptions, diagnoses, and drug dispensing. But, ensuring that only minimal information is shared between these identities, citizen privacy is maintained. The same data is also highly efficient at identifying anomalies before human observers become aware, as in the case of widespread viral outbreaks like the COVID-19 pandemic. ML systems consistently outperform humans in identifying patterns of behavior and have already proven highly accurate at performing some medical diagnoses. The same technologies applied to tracking and tracing can help identify those potentially affected by high-risk interactions.
"Zero-trust" is a term used to describe a secure operating environment, one that acknowledges that trust is a vulnerability. It is not a specific state, but the practice and implementation of security controls that enable a far more granular approach than traditional perimeter security.
Given the overheads of legacy infrastructure, integration in a zero-trust distributed model is the domain of identity-aware proxies; that is, platforms that accept requests to connect, authenticate the source, allow or deny connections to resources, and maintain an audit trail. These platforms allow digitally identified assets — including people, if you recall — to connect to each other from any network or device. This eases and accelerates integration, within a city as well as with external entities.
The key ingredients of a zero-trust model are digitally-transformed trust, security, and integrity. Trust enables interactions, security protects them, and integrity manages them. All three leverage digital identities to interact and enable a truly transformed digital business.
This identity-centric approach is one of the most effective ingredients of digital transformation. Rather than inhibiting business interactions, a zero-trust model enables them by providing a secure, E2E platform in which services, people, hardware, software, and cloud resources are able to interact, with the capability of realigning those interactions and relationships rapidly in response to changing market conditions, without unnecessary overheads.
Disclaimer: The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy, position, products, and technologies of Huawei Technologies Co., Ltd. If you need to learn more about the products and technologies of Huawei Technologies Co., Ltd., please visit our product pages or contact us.