Produkty, Rozwiązania i usługi dla przedsiębiorstw
With the rapid development of the Internet of Things (IoT) and mobile communications, allied to the emergence of a wide variety of new Operating Systems (OSs), the number of terminals requiring network access is proliferating. Indeed, by 2020, the number had already reached approximately 30 billion. Terminals are not only increasing in number, either. They're also becoming more heterogeneous, with IoT terminals such as industrial control and e-healthcare devices being introduced on top of the already commonplace intelligent terminals — think Personal Computers (PCs) — and dumb terminals, such as printers and cameras. Such a rapid increase in the quantity and variety of terminals obviously poses significant and numerous Operations and Maintenance (O&M) and security challenges. Of these, four are key.
To begin with, O&M issues often involve Network Management Systems (NMSs), which can display Internet Protocol (IP) and Media Access Control (MAC) addresses of access terminals, but are unable to identify specific terminal types, limiting refined management capabilities for network terminals.
Next, dumb terminals need to access campus networks through MAC address authentication. This means that network administrators must manually collect and record such MAC addresses, which is a complex, error-prone, and labor-intensive task.
The third challenge relates to security. In certain office scenarios, members of staff can access networks on PCs or cellphones using just a single account. This inability to grant different access permissions, based on terminal types, creates clear security risks.
Finally, as the number of IoT terminals continues to grow across campuses, dumb terminals have become more vulnerable to attacks or spoofing. According to technological research and consulting firm Gartner, nearly 20% of enterprises and organizations have suffered at least one IoT attack over the past three years.
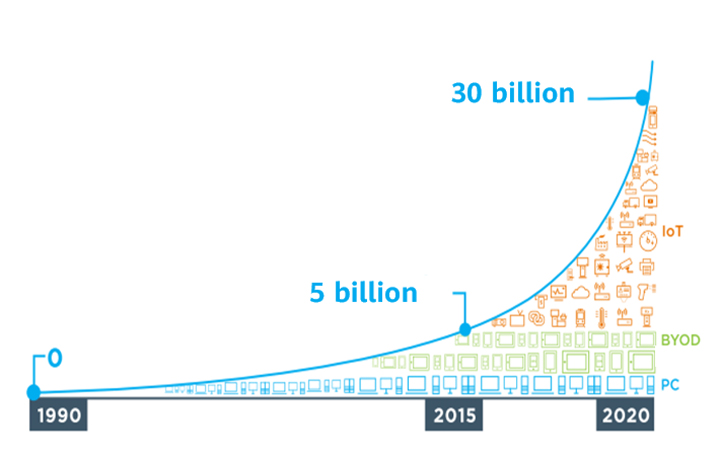
Figure 1: The growth trend of access terminals
In essence, the root cause of the first three challenges lies in the lack of automatic terminal identification capability. After this capability is enabled, however, an NMS can add terminal details, such as terminal types and models, based on their MAC or IP addresses. For terminal MAC addresses to be automatically collected and recorded, authentication-free policies need to be configured on authentication servers, based on online terminal information. In addition, different authorization policies must be configured on the authentication servers, based on terminal types.
That final challenge — vulnerability to attacks or spoofing — is a result of the susceptibility of dumb terminals to forgery, since they typically access networks using weak authentication methods, such as MAC address authentication. Worse yet, due to their often outdated system and software versions, as well as a general lack of scheduled virus scanning and clearing, dumb terminals are further prone to attacks by unauthorized users. To combat this issue and prevent such clear security risks, real-time terminal anomaly detection has to be enabled, with the network access rights of abnormal dumb terminals also closely controlled.
Intelligent terminal O&M is implemented through two awareness technologies — terminal identification and terminal anomaly detection — which improve O&M and security efficiency.
Terminal identification technology comprehensively analyzes and automatically identifies the target attributes — types, vendors, models, and OSs — of terminals. To do so, the technology uses a range of methods, such as passive fingerprint collection and proactive scanning. The former involves the collection of fingerprint information — including the MAC Organizational Unique Identifier (OUI), Dynamic Host Configuration Protocol (DHCP) options, Hypertext Transfer Protocol (HTTP) user-agent, multicast Domain Name Service (mDNS), and Link Layer Discovery Protocol (LLDP) — in a library, to which individual terminal attribute information is then matched and identified. In proactive scanning, terminals are scanned through Simple Network Management Protocol (SNMP) queries, Network Mapper (Nmap) OS scanning, and detection scripts that can be dynamically scaled out. Terminal attribute information is then matched and identified based on the detection response information, as well as information in the fingerprint library.
Equipped with the industry's most comprehensive fingerprint library, Huawei's terminal identification system is capable of identifying more terminal models in office scenarios than competing systems, with an identification accuracy of over 95%.
The second technology, terminal anomaly detection, comprehensively analyzes and determines whether the type, fingerprint, or traffic behavior of a terminal is abnormal, with a key focus on the type and fingerprint. Put simply, the technology identifies a terminal as abnormal if its type or fingerprint information changes. Terminal traffic behavior is also monitored to check for any potential abnormalities.
The terminal fingerprint library is the core asset and crucial foundation behind terminal identification technology. In current network environments, numerous different types of terminals are frequently updated. But terminals vary greatly between industries and obtaining network data samples of terminals in sensitive industries is particularly difficult. Nonetheless, the efficient collection of fingerprint information to create a fingerprint library is of vital importance.
In a conventional approach, terminal identification only determines whether terminal types and fingerprints are abnormal. This is ineffective in certain scenarios, when spoofed terminals construct packets, or terminals are attacked by Trojan horses, for example. Traffic behavior-based terminal identification is well suited to handling these scenarios. However, it remains difficult to obtain traffic behavior models and check the behavior for abnormalities in real time.
The first innovation of Huawei's intelligent terminal management technology introduces an Artificial Intelligence (AI)-based natural language processing algorithm into the analysis and processing of network protocols. This helps discover entities and relationships in the network field as well as construct language models for terminal awareness. Using the algorithm, terminal fingerprint rules can be automatically extracted, facilitating unknown terminal identification on the network.
In addition, Huawei's technology features an AI mining algorithm, which automatically extracts terminal fingerprint rules at an accuracy of over 95%. This addresses the issue of slow terminal identification rates, caused by a large number of terminals, slow updates of the fingerprint library, and the inability to extract terminal rules across sensitive industries.
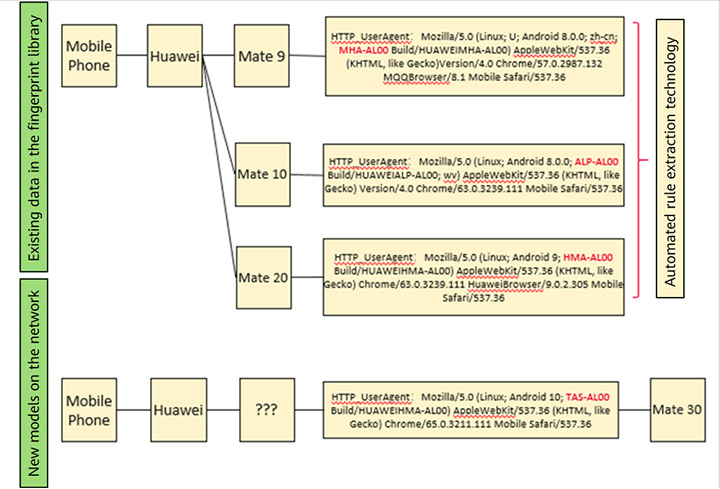
Figure 2: Sample diagram of automated terminal fingerprint rule extraction
In a second innovation, Huawei's intelligent terminal management technology also helps to generate terminal traffic behavior models using AI algorithms, ultimately enabling anomalies to be detected in real time. Traffic behavior characteristics include uplink and downlink traffic statistics, packet lengths, connection quantities, and destination connection statistics, such as IP addresses, port numbers, and protocols.
The terminal anomaly detection system supports two types of traffic behavior models — a preset model and an online-training model — ensuring a terminal anomaly detection accuracy of over 90%. For common terminals, such as cameras, printers, and IP phones, traffic behavior models are generated through offline training and preset in network devices capable of terminal detection. As for unknown terminals, the system collects traffic behavior characteristics online and uses AI algorithms to perform online training and generate traffic behavior models.
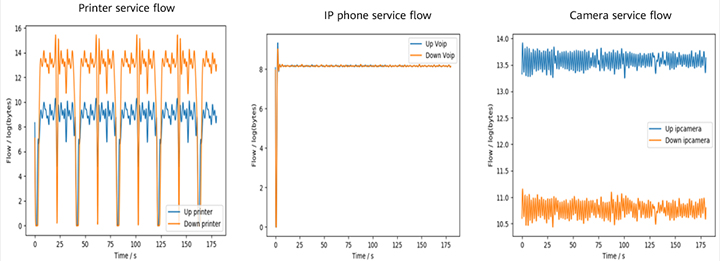
Figure 3: Uplink and downlink traffic behavior characteristics of terminals
In summary, Huawei's intelligent terminal management solution is based on a series of terminal awareness technologies, namely, terminal identification and terminal anomaly detection. It is purpose-built to solve various pain points for customers, from unrefined terminal management and a lack of plug-and-play capabilities, to differentiated terminal strategies and vulnerabilities in terminal security.
This intelligent terminal management solution is best deployed on intelligent campus networks that feature Huawei's own NMS, iMaster NCE-Campus, as well as the company's CloudEngine campus switches, AirEngine Wi-Fi 6 Access Points (APs), and AirEngine Wi-Fi 6 Access Controllers (ACs), with wide applications in the enterprise, government, education, finance, and manufacturing sectors.
Disclaimer: The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy, position, products, and technologies of Huawei Technologies Co., Ltd. If you need to learn more about the products and technologies of Huawei Technologies Co., Ltd., please visit our website at e.huawei.com or contact us.