This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies. Read our privacy policy>
![]()
This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies. Read our privacy policy>
![]()
Enterprise products, solutions & services
Ransomware attacks are now making it into mainstream media headlines — the meat producer JBS in Brazil was recently a victim of a US$11 million cybercrime, the largest cyber ransom in history. Attacks have also disrupted the gasoline supply in the US for weeks.

And there are many, many other cases affecting hospitals, governments, and companies. The 1H 2021 Unit 42 Ransomware Threat Report states that ransom demands increased to an average of US$570,000 in the first half of 2021, up a staggering 82% compared to the previous year. This only represents ransom demands and doesn't even cover the production losses and the enormous damage to reputation for the parties concerned. It is therefore vital for companies and other Information Technology (IT) operators to stay one step ahead by choosing the right solutions.
In principle, there are two different approaches that can be taken. The first involves training employees and the second continues with measures such as deploying endpoint, network, and application security. Given the number of network devices today — think about the sheer number involved in the Internet of Things (IoT) and just how many people who find themselves working from home — achieving 100% security seems impossible. Therefore, solutions are needed to minimize the damage in the event of a successful ransomware attack.
With this in mind, data protection is becoming increasingly important and must be adapted to these attack scenarios in terms of Recovery Time Objective (RTO) and Recovery Point Objective (RPO).
Huawei addresses these issues with its new Data Protection Portfolio.

The portfolio is multi-layered and extends from primary storage to backup destinations and archives, and encompasses business continuity, data recoverability, and regulatory compliance. Active/active or active/passive solutions can be mapped, even across multiple data centers and the cloud, and include archiving to the cloud or to mass storage solutions like OceanStorPacific.
The portfolio is extremely flexible and can be seamlessly integrated into existing environments. Even backup software doesn't have to be changed to achieve many benefits.
At the first level, for primary storage such as OceanStor Dorado, the Hyper Continuous Data Protection (HyperCDP) function was implemented. This can create snapshots of a Logical Unit Number (LUN) every 3s and store up to 60,000 snapshots. As you would expect, consistency groups are also taken into account. The RPO has been reduced to just 3s. This is an enormous improvement compared to conventional backup windows of 24 hours.
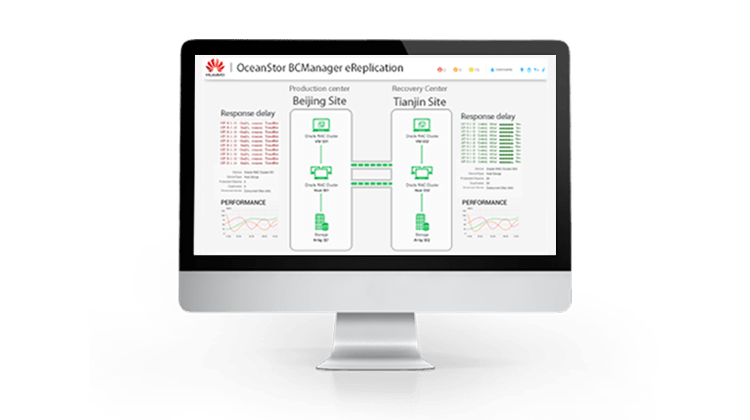
Application-consistent backups and snapshots are created through OceanStor BCManager. This key tool scans application servers for installed applications and installs the appropriate plug-ins. Consistent snapshots and backups can be created and transferred to the backup destination as needed. The HTML5 Graphic User Interface (GUI) also depicts the application and backup structure.

One highlight is certainly OceanProtect Backup Storage. It offers impressive parameters in two performance classes for an efficient and highly available backup destination. Highlights are compression of up to 55:1, 155 TB/h bandwidth, and a maximum storage capacity of 9.2 PB. For this purpose, OceanProtect X8000 and X9000 can be connected with Fibre Channel (FC), Internet Small Computer Systems Interface (iSCSI), Network File System (NFS), and Common Internet File System (CIFS), using up to 32 Gb FC and 100 GE. Different primary storage and a variety of backup software can be used through open interfaces. This makes them a great backup destination for large amounts of data, facilitating rapid backup cycles and allowing data to be restored as quickly as possible.

OceanProtect Appliance is a complete solution. It combines the elements of backup software, backup server, and backup destination into one system, simplifying operations considerably. Backup copies are kept in the original format, reducing the RTO to a few minutes when restoring data. The data is available instantly, without copying, for software development or data analytics. This solution is especially suitable for separate application stacks and small- to medium-sized environments.
Policy-based archiving can be used as the third stage within the data protection architecture. The S3 interface allows, for example, OceanStor Pacific, Blu-ray systems, or the cloud to be used as archive storage. The solution allows legally compliant archiving processes and offers a connection to the overall architecture. This means that archives are immediately accessible for data analytics, as required.
Data can be protected securely and quickly with this flexible, three-stage data protection solution. RTO and RPO are minimized. And even in the event of a ransomware attack, the system environment can be restored efficiently and effectively.
If it is only a matter of replacing backup systems, OceanProtect X8000 and X9000 or OceanProtect A8000 are all great choices.
Disclaimer: The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy, position, products, and technologies of Huawei Technologies Co., Ltd. If you need to learn more about the products and technologies of Huawei Technologies Co., Ltd., please visit our website at e.huawei.com or contact us.