AIFW: The Intelligent Solution For Enterprise Cybersecurity
Produits, solutions et services pour les entreprises
Akıllı Telefonlar, Bilgisayar&Tabletler, Giyilebilirler ve Daha Fazlası
Technology development is a double-edged sword. It benefits enterprises and individuals, but it also arms criminals. The situation of network security has become more severe in recent years, as intelligent and automation technologies can be conducive to new types of cyberattacks that are more diverse, complex, and extensive.
Security incidents are so frequent in companies that they’ve become a major challenge in business development.
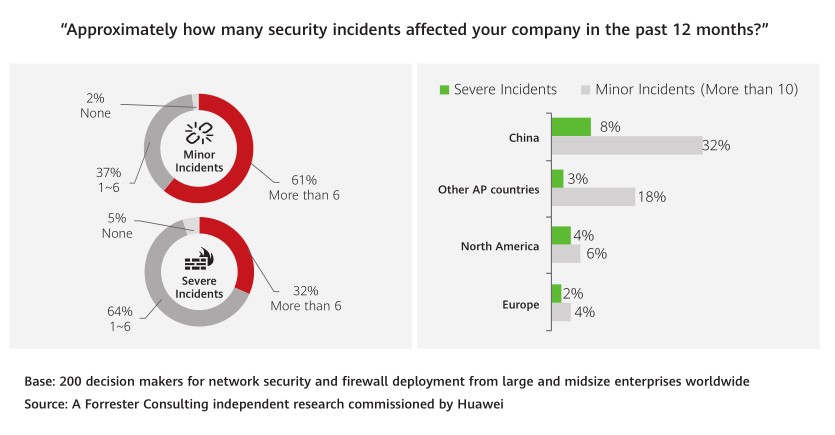
Cyberattacks are complex and diverse
As more applications are exposed to the internet, attempted attacks by cyber criminals grow rampant (see Figure 2). In 2018, CNCERT (China’s National Computer Network Emergency Response Technical Team) captured nearly 140,000 ransomware attacks; and into 2019 this number has continued to rise. Targeted attacks such as the evasion technique, the zero-day exploit, credential theft, and professional phishing are all becoming more sophisticated, and variants of attacks only make things worse. Widespread and continuously evolving hacking techniques and tools may explain the advancement of cyberattacks. Well-planned and organized APTs hinder security analysts of companies using Next-Generation Fire Wall (NGFW) from locating the problem among multiple threats in the cyber kill chain.
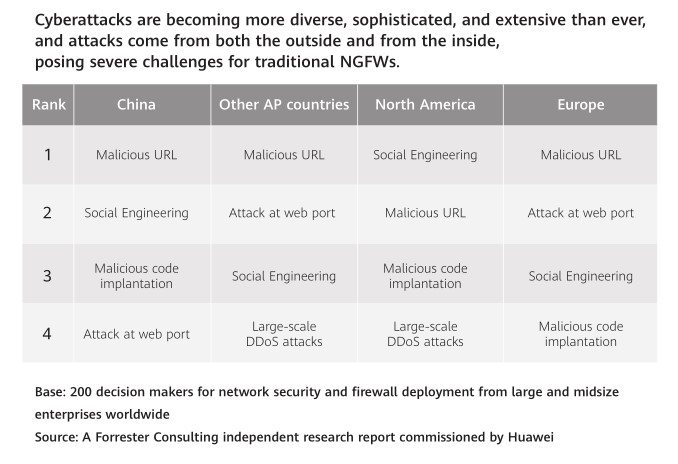
Extensive security attacks
The development of cloud computing, 5G, and the consequent explosive growth of Internet of Things (IoT) have expanded the security boundaries of companies, leading to more extensive cyberattacks. The targets go beyond computers to all exploitable ICT devices, and the attackers originate both from the outside and from within, or as third-party vendors. Internal cyberthreats in particular are harder to detect than external attacks because the attackers have legitimate access to information. Enterprises must increase prevention and protection measures to counter extensive attacks, strengthen the defense lines against internal and external threats, and use other security products to block threats in the entire network.
To defeat evolving threats and attacks, firewall technologies continue upgrading actively to solve problems in performance, operation, and maintenance. Nonetheless, cyber criminals have also made great technical strides over the past decade. Increasingly rampant and intelligent security attacks will severely challenge NGFW’s abilities of prevention and control as we are entering an age of intelligent IP era.
NGFW struggles with rapidly mutating threats
NGFW can identify application vulnerabilities more effectively than previous firewalls, but its rule engine still has significant limitations. The existing solution would generate a signature for a single threat that has been identified, but once the threat mutates, the signature no longer works. This means the NGFW needs to be continuously updating its signature database, which requires person-power to manually renew the solution. However, each local device can only accommodate limited number of signature databases, making it hard to respond to new changes, so the Operation and Maintenance (O&M) personnel have to change the rules constantly, in order to maintain prevention and control capabilities. Through continuous variants of threats, cyber criminals can easily put firewalls to passive responses. Untimely updates open a window for attackers to sneak in. Therefore, the post-event management must intelligently shift the focus from experience to data and insights, to address severe security challenges.
NGFW stumbles in extensive attacks
Cybersecurity threats spread quickly in all dimensions, but NGFW can only protect the preset protocols or applications in the database, and it can do nothing to those outside the database, even if they are of the same type. For intranet attacks, it is critical to swiftly spot the threat and locate the breached computer through means like behavior analysis and abnormal traffic detection, in order to mitigate damage, stop internal diffusion, and build both a comprehensive fence against the Advanced Persistent Threat (APT) attack chain and a detection network that spans the boundary of the enterprise.
NGFW maintenance is stressful
Routine maintenance is critical after NGFW deployment. The O&M personnel update the rules continually for threat mutations. Meanwhile, most NGFWs lack effective data analysis capabilities, requiring O&M personnel to manually analyze massive security logs. Their workload is heavy and demanding, but the effect can’t be guaranteed. Log analysis relies heavily on the experience of security personnel, which undoubtedly increases the company’s investment in operation and maintenance, as well as risks caused by staff turnover.
AI technology can map massive amount of information to high-dimensional spaces with better information abstraction capabilities, bringing new opportunities to security protection with its generalization and inferential capabilities.
AI disrupts the prevention and control of cyberattacks
Threat prevention and control are two primary tasks for any firewall. AI provides more accurate APT detection, more powerful event analysis, and a closed defense loop that spins faster, which greatly enhance the firewall’s ability to prevent and control threats. Specifically, AI can:
Defend new threats effectively.Traditional solutions, based on signatures or rules, are relatively static and struggle to catch up with rapidly mutating threats in proactive defense. AI technology goes beyond the limitations of human beings’ low-dimensional cognition and can better understand the behavioral patterns of threats and attacks at a deeper level. In practice, supervised and unsupervised learning are used to spot frequent variants of malware, locate breached hosts and zombies, detect the theft of encrypted outgoing messages, and identify malicious behaviors like low frequency or distributed brute force attacks. AI learning taps into massive data to generate defense models based on scenario analysis; it upgrades the models continuously according to the real-time data to achieve self-evolution.
Strengthen intelligent analysis of security incidents.Various attacks do leave traces in security logs, but it requires a lot of person-power to detect the threats (from countless logs of operating systems, threats, and network protection) and refine insights to continuously enhance prevention and control capabilities. AI can revolutionize event analysis of cyberthreats. For example, AI knowledge mapping can sort local knowledge such as attack and defense database and threat events, and use them with environmental, behavioral, and intelligence data to dig into data and better detect and defend from threats targeted at critical assets.
Support quicker response to APT attacks.When an intrusion is detected, it is vital to quickly locate and separate the problem and carry out sensible defense. The AI-based APT defense model is more lightweight than traditional solutions and can be easily integrated to the local firewall. Improving on the collaborative external detection in the past, the AI-based APT defense model shortens the exposure time of APT attacks and helps minimize the losses.
AI empowers integrated security protection
AI improves security data analysis and provides better threat detection and prevention capabilities than static rule engines, equipping enterprise firewalls for cyberattacks. AI can also connect equipment in the network for joint machine learning, in order to optimize the defense model on a regular basis.
Federal learning continually optimizes the defense.Restricted by industry sensitivity and policies in some countries, many companies are still uncertain about in-depth sharing of security data with each other. Through encrypted exchanges of parameters, federated learning can improve the sharing model without moving the data, thereby enriching the training data sets for AI to build distributed AI collaborative defenses. AI firewall can also utilize the threat intelligence in the entire network to sustainably and swiftly update the detection and response model to maintain effective defense.
Deploy intranet defense and enhance collaborative detection.A firewall can set built-in traps that will form a safety net for internal threats, using AI-based traffic analysis to identify malicious or illegal traffic for collaborative detection in the intranet.
AI provides necessary tools to improve O&M efficiency
The shortage of senior security O&M personnel is a consensus in the industry. Improving O&M capabilities is one of the most important challenges for the existing prevention and control technology. AI can efficiently analyze massive logs, sparing more time for the O&M personnel. It can also reduce redundancy in security rules through intelligent tuning or even automated generation, reducing the pressure on O&M personnel to maintain huge databases.
In the era of intelligent IP networks, NGFW is severely challenged by increasingly complex security situations, while AI brings new opportunities for enterprise firewalls. This means NGFW should embrace AI and evolve into the Artificial Intelligence FireWall (AIFW) to strengthen prevention and control, to build integrated protection capability, and to improve operation and maintenance efficiency. To make the most out of AI and maximize the prevention and control performance of AIFW, dedicated AI chips, cloud-edge collaboration, and security ecosystem are indispensable for firewall evolution, the reliable safeguard of enterprises, and progression for the entire industry.
AI chips fuel the engine for local apt defense
To build localized defense against APTs, AIFW needs a built-in AI detection engine to respond to threat mutations through self-evolution. Encryption and decryption, packet detection, and traffic forwarding already consume a lot of the computing power of a firewall, but the AI detection engine also demands massive computing power to process mass data and AI inference. Therefore, AI chips are a must-have to enhance computer power for detection, effective emergency response, and other functions of the firewall, providing shorter response time than the cloud’s big data solutions. In principle, the selection of chips should vary due to the diversity of computational tasks, thus dedicated security chips, co-processors, and AI chips will become increasingly important for AIFW.
Build your cybersecurity platform upon extensive collaboration
The growth of IoT applications will extend the security boundaries of enterprises and impact the form of the firewall. Boundary defense requires a collaborative threat detection of AIFWs and other APT defense equipment and clouds.
In the long run, comprehensive security prevention and control also requires extensive alliance in the ecosystem to remain proactive against cyberattacks. Firewalls will need to be open to share or exchange local intelligence for closer collaboration. Companies need to leverage the advantages of partners to share security solutions and experience, which can also promote the development of technologies like AI and IoT and form a virtuous circle. Multiparty collaboration will be critical to securing the victory in the ongoing battle against cyber criminals.
As we enter the age of intelligent IP era, cyberattacks are becoming more diverse, sophisticated, and extensive than ever, posing inevitable challenges for companies. Forrester recommends that:
AI empowers the next generation of firewalls — the AIFW. As a general-purpose technology, AI will be applied widely in various business scenarios, including cybersecurity. For cyberattacks already armed by intelligent technologies, firewalls based on rule engines are obviously outdated. Enterprises should turn to AIFW for comprehensive local defense against APTs. Adopt AI chips to accelerate task processing and collaborate with AI capability centers on the cloud to continuously update security models and ensure cybersecurity in all aspects.
Embrace intelligent applications to improve the O&M efficiency. Intelligent and automated operation and maintenance is the choice of the times. AI-enabled applications like traffic analysis, threat detection, and behavior identification reduce the workload of O&M personnel. The AI-driven intelligent tuning of security rules solves the problems of manual updates, and greatly improves O&M efficiency. As AI detection of unknown threats gets more accurate, false alarms will be significantly reduced, bringing on another leap in O&M quality.
Build your cybersecurity platform upon extensive collaboration. Cyber criminals only exploit a single breach at one time, but the company needs comprehensive defense for being at a disadvantage. As attacks go rampant, companies must collaborate and embrace an extensive ecosystem, share security intelligence, and use information from the entire network to build increasingly powerful security models and to jointly win the battle against cyber criminals.
