This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies. Read our privacy policy>
![]()
This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies. Read our privacy policy>
![]()
Enterprise products, solutions & services
Traditionally, security capabilities are deployed at the border of enterprise networks to defend against external intrusion. As the most typical security gateway device, the firewall is usually deployed at the network border to block threats. However, enterprise network borders become more and more blurred due to the rapid development of emerging technologies and the popularization of remote office and multi-data center interconnection. Security threats change following IT infrastructure trends such as border removal, cloudification, and servitization, traditional security protection measures cannot effectively cope with risks. Therefore,"zero trust" is born and quickly becomes a hit in the industry.
Zero trust is designed to build a relatively trusted relationship by using different techniques and ensure the security for the service and data running. However, this relationship is changing, effective only in a short period of time. It needs to be continuously built to ensure long-term trustworthiness. Zero trust is not a new technical architecture. It uses many common and mature technologies in the security technology graph, such as identity and permission management, proxy gateway, and risk assessment. Therefore, the concept of "zero trust" is easily understood since first proposal, and is widely accepted by security practitioners. In the zero-trust solution, the firewall plays an important role as always and constantly offers new capabilities.
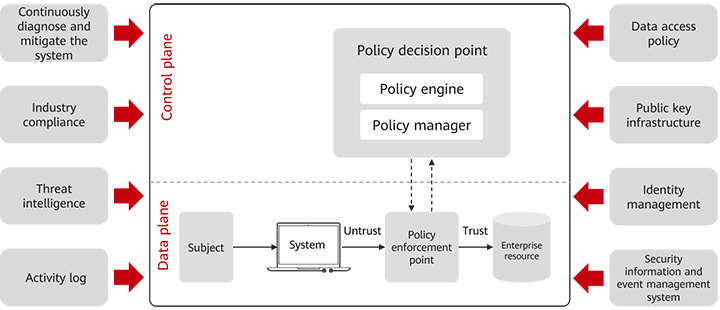
In the typical NIST zero-trust architecture, the core components include policy decision points and policy enforcement points. The policy decision point consists of the policy engine and policy manager. The policy engine is mainly responsible for comprehensively analyzing multi-dimensional risk information, and finally determining whether to allow a specified subject to access an object. The policy manager is responsible for establishing a logical connection between the access subject and the object, generating an access credential. At the same time, the policy manager communicates with the policy enforcement point and executes the policy through it. The policy enforcement point determines whether to allow the subject to connect to the object according to the policy delivered by the policy manager. Multiple components, such as the proxy endpoint and gateway, can act as the policy enforcement point.
Figure 1 shows the NIST zero-trust logical architecture.
Figure 1 Logical architecture of NIST zero trust
Traditional firewall capabilities can be greatly integrated into the zero-trust solution. For example, the detection capability of traditional firewalls is an important source of risk information for the zero-trust policy engine. Its IPS and antivirus capabilities can effectively identify known and unknown threats, which are critical for detecting encrypted traffic. After the risk information identified by the firewall is reported to the zero trust policy engine, the zero trust policy engine can perform risk assessment more comprehensively. In addition, the firewall dynamically blocks or permits traffic based on the comprehensive evaluation result.
In east-west traffic protection, firewalls work with microsegmentation, one of the three key technologies of zero trust, to safeguard the mutual access (east-west traffic) between user endpoints on the campus network and between server resources in the data center. Microsegmentation, also called EPG-based security quarantine, groups resources on a network based on rules. It applies traffic detection and control policies based on EPGs to simplify O&M and implement security management and control. Firewalls equipped with microsegmentation are deployed at different service borders to establish application-level groups, preventing various threats from spreading among service resources. As such, this kind of firewall, serving as "watertight compartment", excellently protects key services. The microsegmentation firewall solution does not rely on the installation of authentication or environment awareness clients on the endpoint, and does not simply deploy 5-tuple ACL on the production intranet to block communication. Instead, it introduces in-depth detection and attack identification capabilities based on Layer 4 to Layer 7 protocols from the network border to the intranet through network behavior analysis, analyzes protocols and detects advanced threats. This capability can effectively block attack packets and malicious traffic mixed in legal communication. In this way, the attack is effectively blocked when key intranet resources provide normal communication services.
As an inherent gateway, the firewall is the most common and reliable policy enforcement point. In a zero-trust solution, a firewall is often referred to as a zero-trust gateway. As a policy enforcement point, the zero-trust gateway mainly implements the access proxy and policy enforcement to the access subject. Based on different scenarios, zero-trust gateways can be classified into application proxy gateways, API gateways, SDP gateways, and IoT gateways.
1. Application Proxy Gateway
In the traditional application access mode, the application address is exposed on the network so that users can access the application at any time. Therefore, attackers can easily scan and probe applications, launch DDoS attacks, or exploit vulnerabilities to infiltrate applications, greatly increasing application security risks. To avoid these risks, more and more applications start to provide services in proxy mode, making application proxy gateway popular gradually.
The main function of the application proxy is to identify the access subject and provide a proxy when the subject accesses the web application. In addition, the application proxy gateway obtains authorization information from the policy manager and performs access control actions such as allowing access, performing secondary authentication, or blocking access.
Figure 2 shows the main functions and peripheral relationships of the application proxy gateway.
Figure 2 Diagram of application proxy gateway functions
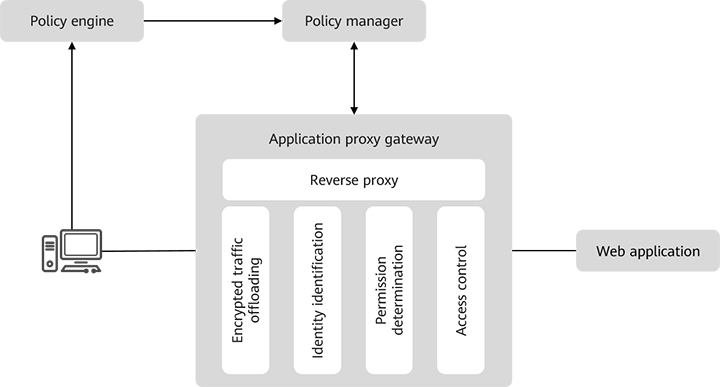
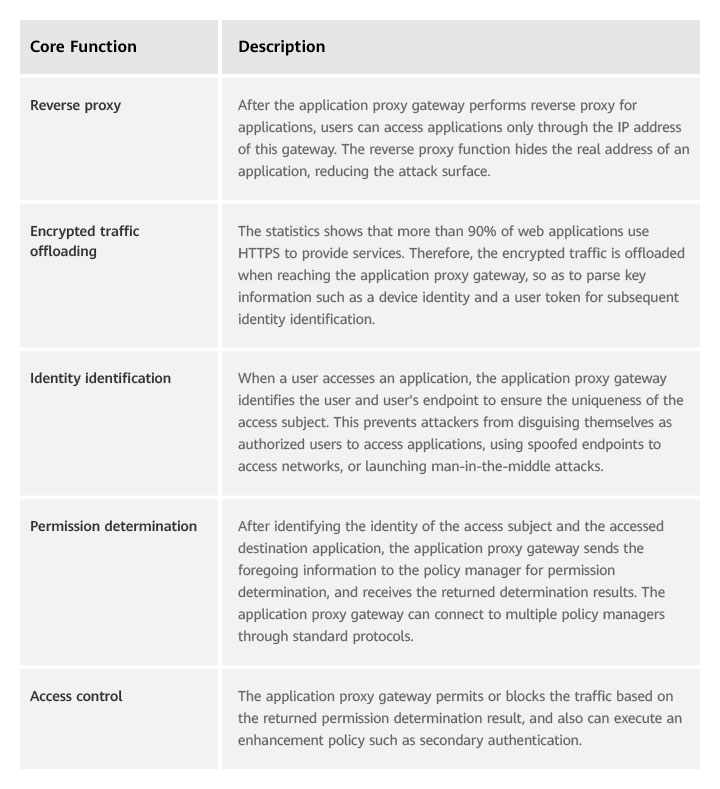
Table 1 describes the core functions of the application proxy gateway.
Table 1 Core functions of the application proxy gateway
2. API Gateway
Nowadays, service-based applications have become a trend. A service is registered with a unified service management platform and opened to applications by calling APIs. In this mode, applications are decoupled from services, greatly improving service sharing efficiency. For example, a map vendor provides a positioning service based on geographical location information, while other applications such as taxi hailing and group buying implement the positioning function only by subscribing to the service. API gateway, as a management platform for registering and releasing services,
shares similar functions with the application proxy gateway. The difference is that the former provides access control when applications call APIs, while the latter provides access control when users access applications. When an application calls an API of a service, API gateway provides proxy forwarding and access control services. API gateway hides APIs to reduce the attack surface. Therefore, the API gateway may also serve as a policy enforcement point to receive policies delivered by the policy manager and perform the API-level access control.
Figure 3 shows the main functions and peripheral relationships of API gateway.Figure 3 Diagram of API gateway functions
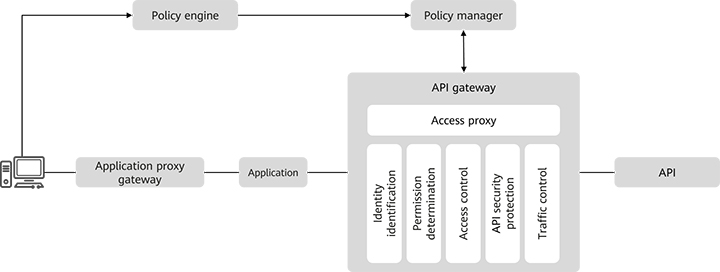
The API gateway shares similar core functions with the application proxy gateway. The only difference is that the proxy object is changed from an application to the API gateway. API gateway performs proxy forwarding, identity identification, and permission determination for API requests. API-level access control is a permission control finer-grained than application-level access control. API gateway also provides the functions listed in Table 2.
Table 2 Other core functions

3. SDP gateway
It is well known that SDP is one of the three key technologies of zero trust. The SDP framework proposed by Cloud Security Alliance (CSA) in 2013 attracted much attention in the industry. As a typical next-generation network security model based on the zero trust, the SDP framework does not focus on the physical boundaries that traditional security solutions dedicated to. Instead, it focuses on service resources. By constructing a virtual boundary that varies with service locations, the SDP framework adapts to the cloud era where network boundaries are gradually blurred, effectively protecting data security.
Figure 4 shows the overall architecture of the SDP gateway.
Figure 4 SDP framework
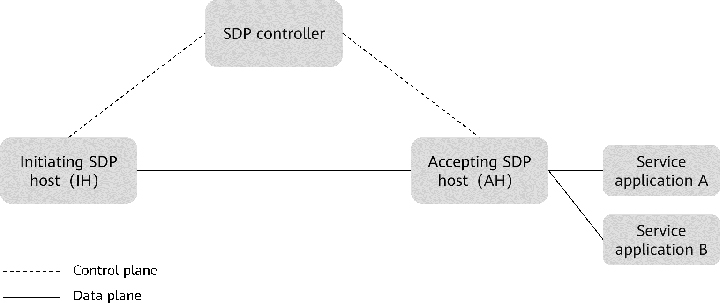
In the SDP solution, the accepting SDP host servers as the policy enforcement point to control the connection from the access subject to the access object (any accessible resource or service). The accepting SDP host is also called an SDP gateway depending on its location and function.
Table 3 describes the features of the SDP solution architecture.
Table 3 Features of the SDP gateway

4. IoT gateway
The Internet of Things (IoT) has gradually become one of the important scenarios for enterprise informatization. IoT generally uses IoT communication protocols, such as Bluetooth and Zigbee. Therefore, it is quite important for an IoT gateway to support common IoT communication protocols, and connect to and manage IoT devices. Unlike other zero-trust gateways, IoT gateways generally do not need traffic proxy.
Figure 5 shows the main functions and peripheral relationships of the IoT gateway.
Figure 5 Diagram of IoT gateway functions
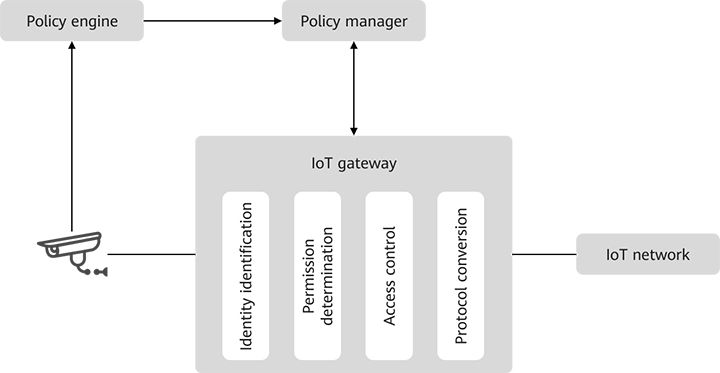
The IoT gateway must also have capabilities such as identity identification, permission determination, access control, and protocol conversion, and support IoT communication protocols.
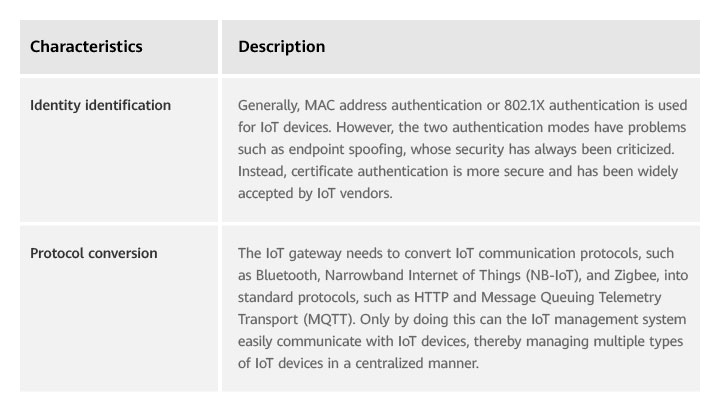
Table 4 describes the main features of the IoT gateway.
Table 4 Main features of IoT gateways
All in all, zero trust is not an innovation in technologies, but an innovation in concepts and technical architectures. With the concept of "Never trust, always verify" and various mature security capabilities, zero trust builds a brand-new security system. The firewall perfectly complies with the principle of minimum authorization and continuous monitoring of all traffic, which helps the zero trust solution ensure the security of all accessed resources at any access location. In addition, the firewall keeps self-innovation and continuously performs dynamic identity verification, permission change, and policy execution automatically based on environment changes to improve efficiency and security. Firewalls in the new era are fully integrated into the zero-trust solution, making the solution more competitive and effectively protecting data security.
Disclaimer: The views and opinions expressed in this article are those of the author and do not necessarily reflect the official policy, position, products, and technologies of Huawei Technologies Co., Ltd. If you need to learn more about the products and technologies of Huawei Technologies Co., Ltd., please visit our website at e.huawei.com or contact us.